SourceIntel is an UnpacMe open source intelligence (OSINT) enrichment service that collects technical and contextual information about binaries observed in the wild.
Primary source collection is obtained via web crawlers, social media monitoring, botnet emulators, and passive collection sources such as honeypots and spam traps.
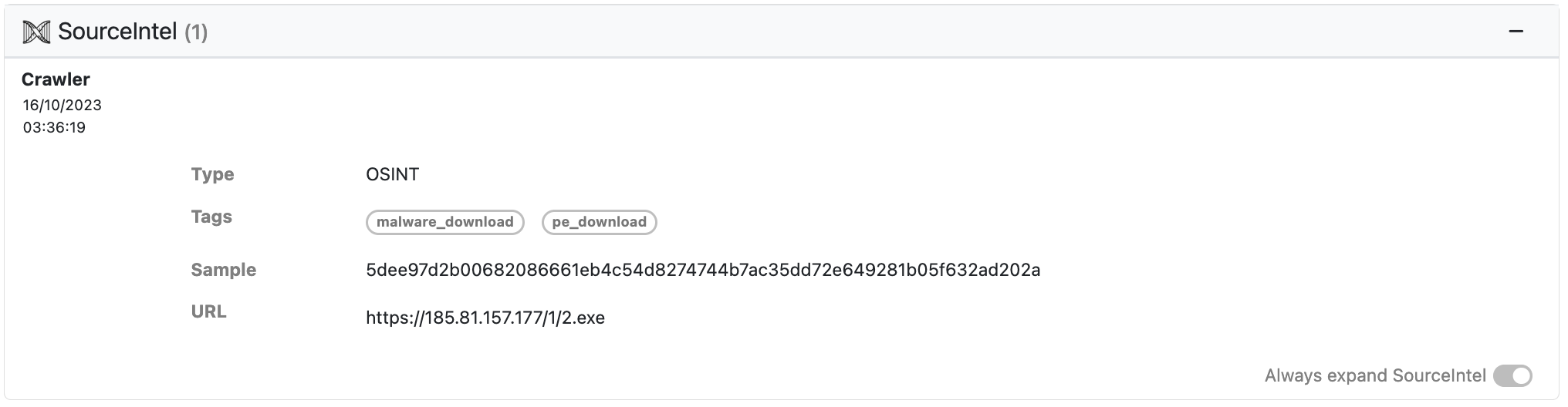
For each submission to UnpacMe the SourceIntel database is queried for enrichment information on the Parent file and is displayed in the SourceIntel window at the top of the Results page.
For each enrichment the Source of the information and the date it was collected are supplied along with the following standard information.
- Type – The type of collection. Not to be confused with the Source the type refers to the collection type, either OSINT, or PROPRIETARY. OSINT information is collected from open sources while PROPRIETARY information is generated using internal processes. Botnet command and control emulation is an example of PROPRIETARY information.
- Tags – A list of tags used to classify the information collected.
- Sample – A hash (MD5, SHa1, SHA256) linking the collected information to a binary.
A non-exhaustive list of SourceIntel collectors follows.
- SourceIntel – The SourceIntel collector label is used to mask internal collection processes that are not exposed for operational security purposes.
- Crawler – Internet scanning of known binary drop sites.
- Opendir Scanner – Recursive scanner seeded with botnet command and control URLs.
- Twitter – X (formerly Twitter) monitoring.
- Pastebin - Pastebin monitoring.
By default the the SourceIntel window is displayed when navigating to the Results page though the default setting preference can be controlled in the Account Settings..
