UnpacMe maintains a framework of malware configuration extractors used to extract information from known malware families such as the command and control (C2) addresses, cryptographic keys, and other settings used to control the behaviour of the malware.
Malware Config Overview
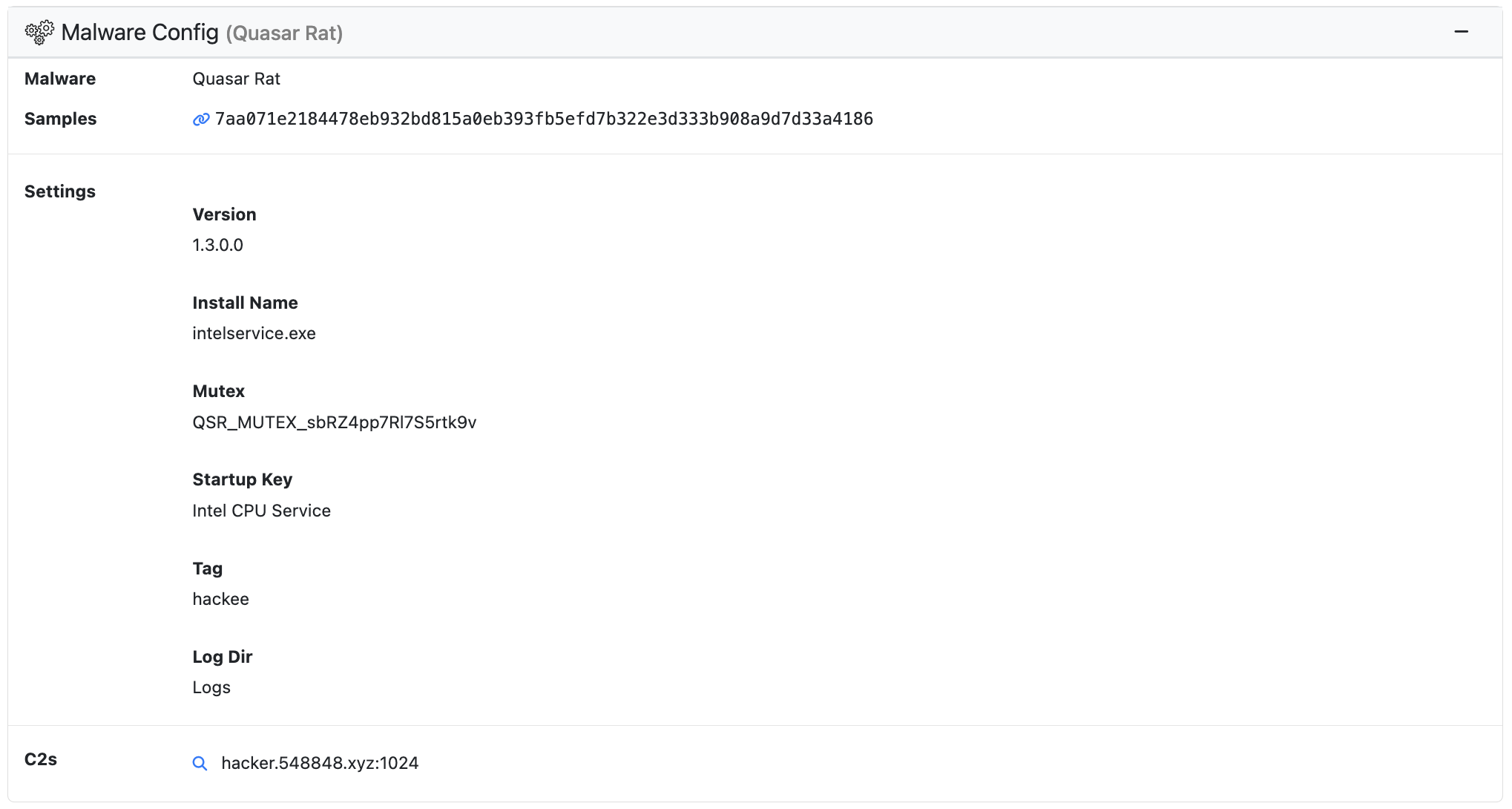
During analyst multiple malware configs may be extracted depending on the number and variety of malware Children unpacked from a Parent. An overview of each config is displayed at the top of the Results page in the Malware Config window. This window displays the name of the malware family associated with the config, a link to the sample that the config was extracted from, any extracted C2s, and a brief overview of the config settings.
It is important to note that the full config settings including any decrypted strings are NOT displayed in the overview window.
Full Malware Configuration
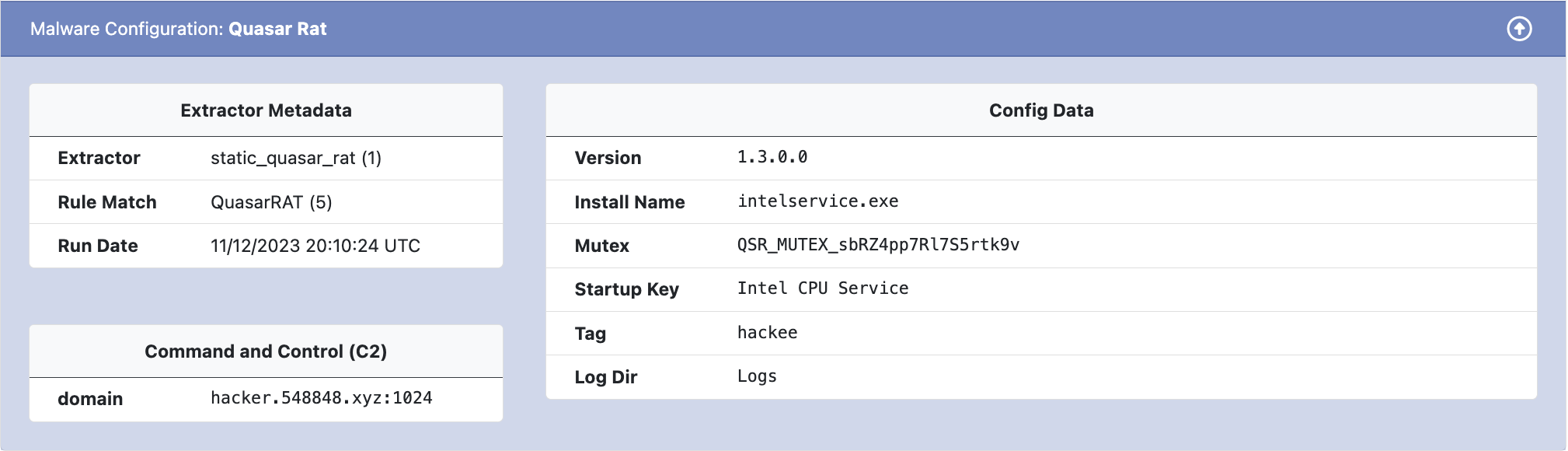
The full configuration information is displayed in the configuration entry below the sample window. The config title can be clicked to display the full config.
Extractor Metadata
Each configuration file contains metadata with information about the extractor process.
- Extractor – The Extractor field displays the name of the configuration extractor module followed by the module version in
(). - Rule Match – The Rule Match field displays the name of the rule that triggered the extractor module followed by the rule version in
(). - Run Date – The Run Date field displays the date that the config was extracted.
Command and Control (C2)
C2 information refers to domains, IPs, and URLs used by the malware to receive commands and upload data. Extracted C2 information is displayed separately from other configuration settings.
Config Data
Config Data refers to all extracted settings and information other than C2 information. Settings are displayed unstructured in key-value pairs.
Decrypted Strings
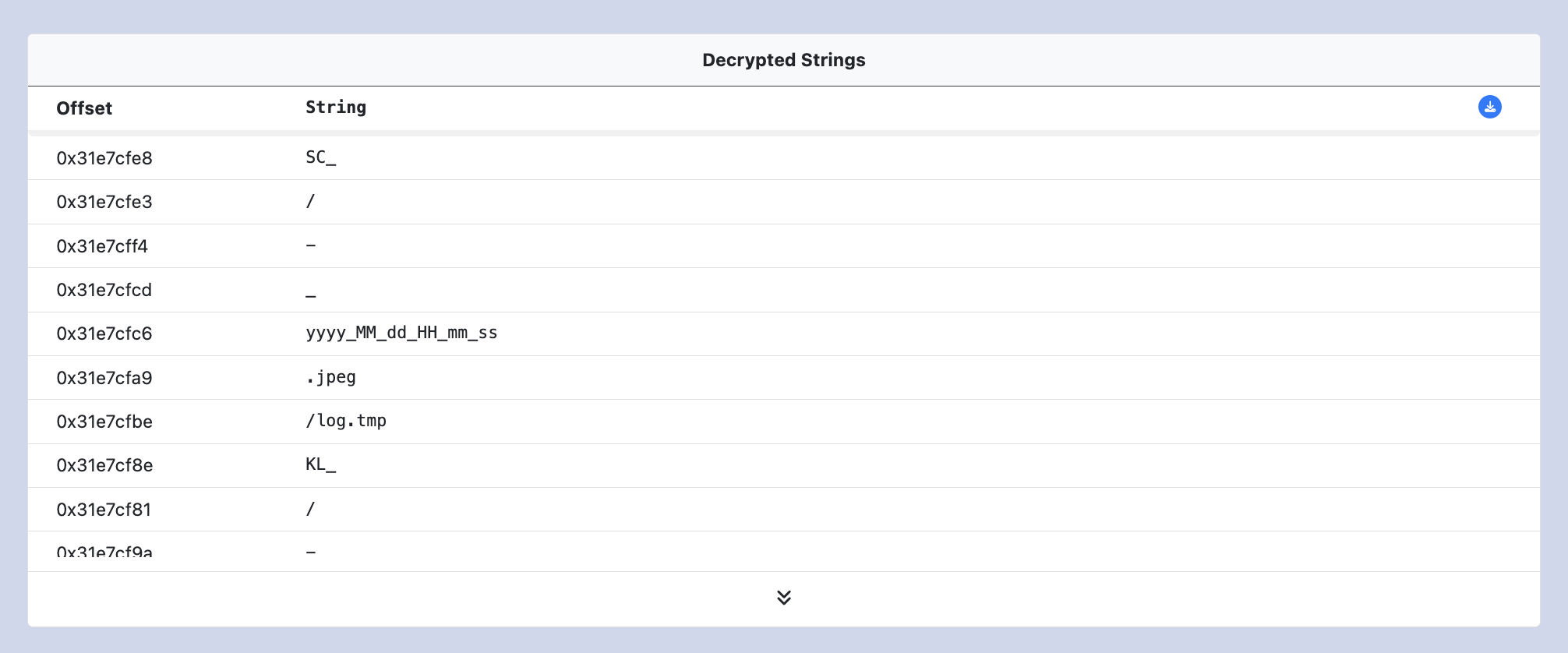
Where applicable encrypted strings in that malware are extracted and decrypted. They are displayed along side their offset in the binary. In cases where the string is not referenced via an offset (for example .NET tokens) the strings are arranged in numerical order.
The Decrypted Strings table can be downloaded as a JSON file by clicking the download button in the top right corner of the window. This JSON file can be imported into IDA Pro and used to annotate the IDB using the StrAnnotate-IDA plugin.
