ATIP is an AI-powered service designed to translate malware analysis into threat intelligence. By automatically summarizing malware analysis results, ATIP quickly generates detailed threat reports, highlighting key insights on malware behaviour, capabilities, and overall threat potential.
ATIP produces three types of reporting, direct malware behaviour summaries (currently limited to script based malware), high level malware family summaries, and detailed threat reports (PDF).
Malware Behaviour Summary
ATIP automatically enumerates the capabilities of script based malware in quickly ingestible heads up summaries.
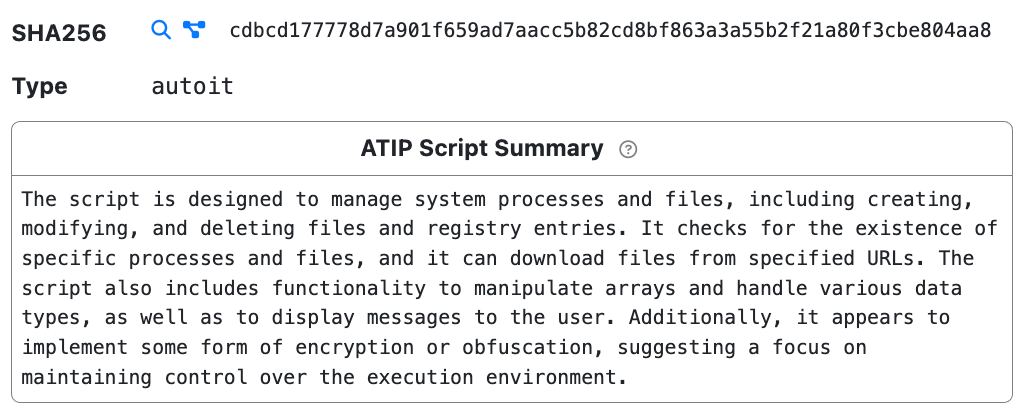
Malware Family Summary
Malware analysis results for specific malware families are summarized by ATIP and provided as a short digest. The summary is accompanied by a ten-week trend chart. This chart displays the relative volume of the observed malware family as a percentage of total malware, highlighting overall trends in its prevalence.
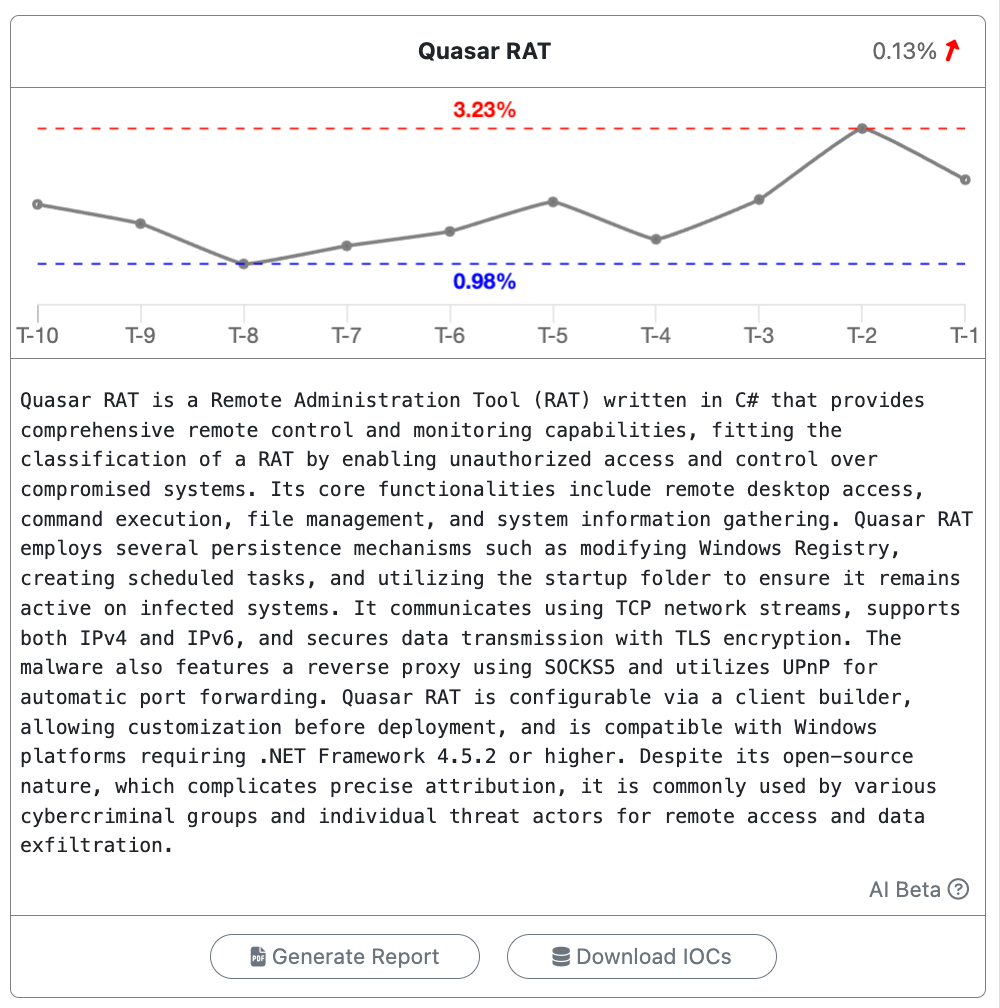
Threat Intelligence Reports
Analysts can task ATIP with generating an in-depth threat report for any malware family that has an ATIP Malware Family Summary. The generated report combines UnpacMe analysis results with internal analysis notes, observed malware behaviour, and OSINT to produce a holistic threat picture for the malware.
ATIP reports are generated on demand, ensuring that each report reflects the latest available information. As analysis is continuously updated, regenerated reports may vary in language and content, providing the most accurate and current threat intelligence possible.
The threat reports include a description of the malware, its capabilities and characteristics, as well as associated operators and attribution when known. Reports also include an ATT&CK matrix for the malware, and recently observed IOCs associated with the malware.
Malware IOCs
Users who have subscribed to the UnpacMe Feed also have the option to download IOCs associated with the malware family. IOCs are provided in JSON format which can be programmatically ingested into SIEM and threat intelligence platforms.
